WHAT IS FIREWALL ?
A firewall is a device or set of instruments that allows or disallows network transmissions based on a set of rules and regulations. Firewalls are commonly used to protect networks from cyber-attacks.

Illegal access while genuine communications are allowed to pass or during the transmission of sensitive data Distributed
Firewalls allow a network’s security regulations to be enforced. without being constrained by an inside or outside point of view
Using a policy language and delegating authority to a central location support for all members of the network domain semantics
firewall technology in the context of organisations gadgets connected to the internet still converse across unsecured channels allow for the logical separation of hosts within and outside the trusted zone domain. The general concepts of such distributed systems are introduced.
We discuss the general ideas of such distributed firewalls, their needs and ramifications, as well as their applicability for prevalent Internet threats.
Computers and networking are now inextricably linked. Every second, a large number of confidential transactions take place, and computers are now mostly utilised for data transmission rather than processing. As a result, network security is required to prevent data hacking and to ensure secure data transit. The use of a firewall can help to secure a network.
To function, traditional firewalls rely on the concepts of constrained topology and regulated access points. The evolution of Distributed Firewalls is due to network topology restrictions, difficulty filtering particular protocols, End-to-End encryption issues, and a few other issues.
DISTRIBUTED FIREWALL
A distributed firewall is a technique for enforcing a network domain security policy using a policy language, a policy distribution scheme that allows policy control from a central point, and certificates that allow any member of the network policy domain to be identified.
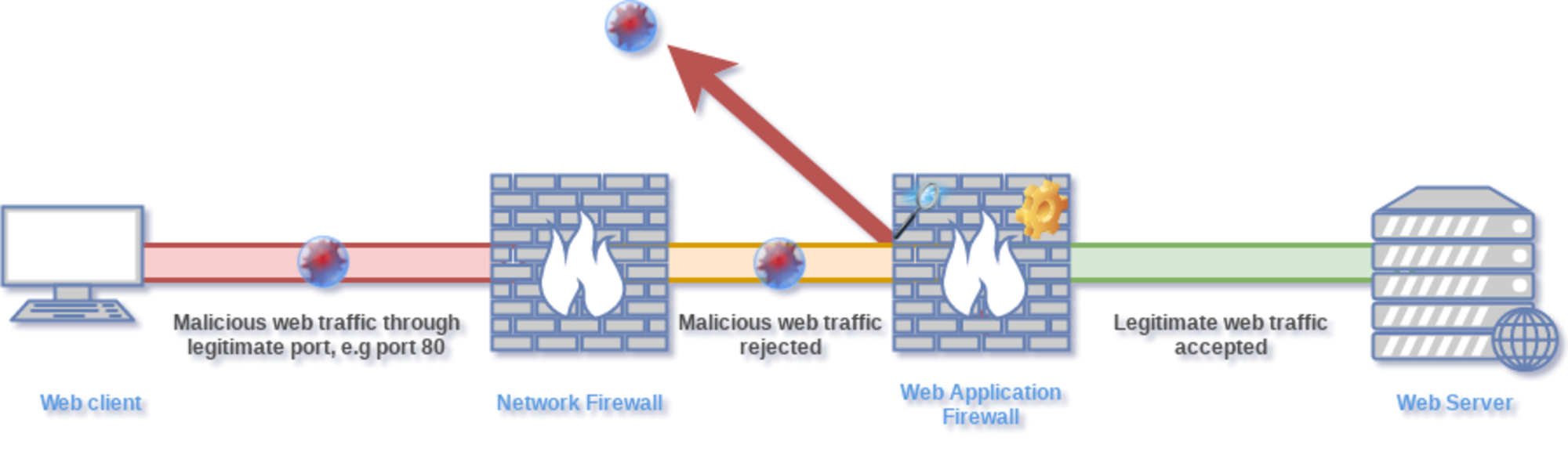
Distributed firewalls defend the network by securing crucial network endpoints, which are the most vulnerable to hacking. Because the most damaging and costly hacking assaults still come from within the business, it filters traffic from both the Internet and the internal network. They offer nearly limitless scalability. Additionally, they eliminate the perimeter firewall’s single point of failure concern.
Distributed firewalls are host-based security software solutions that safeguard the servers and end-user machines in a business network against unauthorised access. They have the benefit of filtering traffic from the Internet as well as the internal network. This allows them to defend against hacking assaults that originate on the Internet as well as on the internal network. This is critical since the most expensive and damaging attacks still come from within the corporation.
CONVENTION FIREWALL PROBLEMS
A firewall is a set of components that sits between two networks and filters traffic according to a set of security policies.
There are some issues with traditional firewalls that lead to
The following are examples of distributed firewalls.
1) It is dependent on the network’s topology.
2) Networks should not be protected against internal attacks.
3) Protocols such as FTP and RealAudio are not supported.
4) Has a single entrance point that can fail, causing difficulties.
5) Incapable of terminating “spoof” transmissions (i.e., using false source addresses).
6) They are unable to track all network activity and dynamically open and reopen networking ports.
FIREWALL DESIGN TAKES A DISTRIBUTED APPROACH
It is no longer possible to maintain a fixed network architecture because of the huge increase in network complexity and the emergence of new technologies such as wireless networks and VPNs. User needs for mobility, security, performance, and reliability are also increasing. As a result of these and other drawbacks, traditional
Firewalls are becoming increasingly ineffective. Bellovin and Ioannidis, et al. developed the distributed firewall idea to address such issues.
The distributed firewall concept is focused on implementing policy rules at endpoints rather than at a single network entry point. Security policies are still set at a high level. The goal of this strategy is to keep the benefits of firewalls while addressing the drawbacks listed below.
Distributed firewalls are founded on three concepts.
– Policy wording: This is required in order to specify which types of connections are acceptable and which are not.
– System management tools such as SMS or ASD from Microsoft.
–IPSEC is an example of a network-level encryption technique for TCP/IP.
Using these concepts, a distributed firewall system operates as follows. A tool or a compiler is used to translate the policy language into an internal format. This policy data was provided by the system management tool to all of the hosts protected by the firewall. The arriving packets are then accepted or refused at each host based on the sender’s security policy and cryptographic verification.
The centralised management of security policies is one of the most important aspects of a distributed firewall system. Centralized management is critical for such a vast and complicated system, as it ensures consistency across all firewall devices in the system, which improves security. Another important element to remember is to distribute policies in a secure manner. To do so, security services must be used to ensure the integrity, confidentiality, and authenticity of security policies.
Policy Based Network Management (PBNM) is a new network management solution that abstracts network administration tasks by providing a system-wide management and configuration approach.
PBNM treats the network as a whole and attempts to manage it as a single unit, in contrast to typical management systems that focus on device characteristics. With the support of centralised storage, creation, and management of network policies, PBNM accomplishes this abstraction. This is highly useful for providing system-wide device configuration uniformity, efficiency, dependability, and a dynamic approach. When it comes to administering security policies in a distributed firewall, such details are critical.
DISTRIBUTED FIREWALL ADVANTAGES AND DISADVANTAGES
The emergence of distributed firewalls provided some solutions to problems that were difficult to solve with traditional firewalls. Distributed firewalls have a number of advantages.
It’s possible to put it this way:
• Distributed firewalls have a number of advantages, including topological independence. Because network security is no longer dependent on network topology, the security perimeter may be defined with greater freedom. When necessary, the security perimeter can be readily extended to cover remote hosts and networks.
• Unlike traditional firewalls, network security is no longer reliant on a single firewall to manage issues such as performance bottlenecks and traffic congestion.
Furthermore, because much of the filtering is done at the end hosts, the load on the traditional firewall is decreased.
• As previously stated, filtering some protocols such as FTP is difficult with a traditional firewall. On distributed firewalls, this process is much easier because all of the necessary information is available at the decision point, which is usually the end host.
• In terms of network administration, the number of outbound connections does not provide as many challenges. The network security is unaffected by adding new links or eliminating existing links. In distributed firewalls, backdoor connections formed by insiders, whether intentionally or unwittingly, do not pose a new danger to network security.
• As previously stated, traditional firewalls make the assumption that insiders are trustworthy. However, this assumption leads to a slew of issues. Insiders are no longer treated as “unconditionally trustworthy” with distributed firewall architectures. With distributed firewalls, dividing a network into portions with different security levels is much easier.
• On a need-to-know basis, security policy rules are distributed and defined. The applicable policy should be determined only by the host that needs to communicate with the external network. This method greatly simplifies policy updates and eliminates the need for each firewall to retain the entire policy set.
• In distributed firewall systems, end-to-end encryption is achievable without compromising network security. The usage of end-to-end encryption in traditional firewalls was producing some network security issues. End-to-end encryption, on the other hand, considerably increases the distributed firewall’s security.
However, there are certain disadvantages to
The following is a summary of distributed firewalls:
• One of the key difficulties with distributed firewalls is compliance with security policies for insiders. This difficulty is exacerbated when each ending host has the ability to change security policies. There are several strategies that can be used to make changing policies more difficult, but it is not completely impossible to avoid.
• In a distributed firewall environment, implementing an intrusion detection system is difficult. Suspicious connections can be logged locally, but these logs must be gathered and reviewed by security professionals in central services.
POLICIES
Policy is one of the most commonly used terms in network security, particularly in the context of distributed firewalls. Being aware of policies is essential.
A system’s security regulations are defined by a “security policy.” There is no way to determine what access is permitted or prohibited without a clear security policy.
The following is a simple firewall example:
-Allow all connections to the web server to be accepted.
-Restrict all other access.
The policy’s distribution can differ depending on how it’s implemented. It can either be pushed directly to end systems or pulled as needed.
A. Pull technique
While the hosts are booting up, they ping the central management server to see if it is up and running. It connects to the central administration server and asks for the policies that it should follow. The host’s security policies are provided by the central administration server. A licencing server or a security clearance server, for example, could be queried if a particular communication should be allowed. A traditional firewall could perform the same thing, but it would be missing crucial information about the request’s context. End systems may be aware of details such as which files are involved and their security levels. Such data could be sent across a network protocol, but only if it was made more complicated.
B. Push technique
When the network administrator updates the policies on the central administration side and the hosts must be updated instantly, the push mechanism is used. This push method ensures that hosts have access to the most recent policies at all times. The policy language specifies which inbound and outbound connections are permitted on any component of the network policy domain, and it can influence policy decisions at any layer of the network, such as whether certain packets are rejected or passed, or whether policies are enforced at the Application Layer.
A DISTRIBUTED FIREWALL’S COMPONENTS
- A policy-making system with a central administration system.
- To broadcast these policies, you’ll need a transmission system.
- Client-side implementation of the designed policies.
A. System of central management
A component of distributed firewalls, central management, makes it possible to secure enterprise-wide servers, desktops, laptops, and workstations. Central management improves control and efficiency while lowering the cost of maintaining global security systems.
By allowing policies to be centrally defined, deployed, monitored, and updated, this feature meets the need to maximise network security resources. Distributed firewalls can be scanned from a single workstation to discover the current operating policy and whether it needs to be updated.
B. Policy dispersal
The policy distribution mechanism should ensure the policy’s integrity during the transfer. The policy’s distribution can differ depending on how it’s implemented. It can either be pushed directly to end systems or pulled as needed.
C. Implementation of the host-end
The host must implement the security policies supplied from the central management server. The network administrator does not have any administrative control over the application of policies from the Distributed Firewall’s host end. Based on the security policies it has set, the host authorises traffic.
COMPONENTS OF A FIREWALL FOR A DISTRIBUTED FIREWALL
In their most basic form, policies in a distributed firewall are functionally similar to packet filtering rules. However, it is preferable to utilise a system that can be expanded (so that othertypes of applications and security checks can be specified and enforced in the future). Credentials for delegation of rights and authentication should be supported by the language and resolution mechanism.
When possible, the IPsec keymanagement protocol or another protocol can be used to safely distribute security policies. Either through the communication protocol or as part of the policy object description, the integrity of the policies conveyed must be guaranteed (e.g. they may be digitally signed). The enforcement part is provided by a system that applies the security policy to incoming packets or connections.
CONCLUSION
The goal of this work is to find a solution to computer crime, which implies that a user can send sensitive and critical data or information while being protected by firewalls and distributed firewalls. They are responsible for the legal framework that allows people to use the internet. Firewalls include features such as allowing only authenticated users to use a computer or the internet for personal purposes. In this work, we attempted to describe or demonstrate internet challenges and their solutions using distributed firewalls. It’s also known as the filtration procedure.
Firewalls are important in many places, such as colleges and other institutions, for data and network security. As a result, this is our single document attempting to raise awareness and propose a solution for networking through distributed firewalls.


