An Intrusion Detection System (IDS) is a network traffic monitoring system that detects suspicious behaviour and sends out notifications when it is found. It’s a piece of software that searches a network or system for malicious activities or policy violations. Any harmful activity or violation is usually reported to an administrator or collected centrally using a SIEM system. A SIEM system uses alert filtering algorithms to discriminate between malicious and false alarms by combining data from several sources.
Although intrusion detection systems monitor networks for suspicious activity, false alarms are common.As a result, when enterprises first implement IDS products, they must fine-tune them.
Intrusion prevention systems also monitor network packets entering the system to look for malicious activity and provide warning signals immediately.
What are the workings of intrusion detection systems?
Intrusion detection systems detect irregularities in the network, allowing hackers to be identified before they cause significant damage.”
Network-based IDSes and host-based IDSes are both possible. A host-based intrusion detection system is installed on each client computer, whereas a network-based intrusion detection system is installed on the network.
Intrusion detection systems look for signatures of prior attacks or deviations from normal behaviour to detect attacks. As they progress up the stack, these abnormalities are investigated at the protocol and application layers. For example, they can detect things like Christmas tree scans and DNS poisonings.
An intrusion detection system (IDS) can be used as a client-side software programme or as a network security device.To safeguard data and systems in cloud deployments, cloud-based intrusion detection solutions are now available.
Intrusion Detection System Classification:
There are five types of IDS:
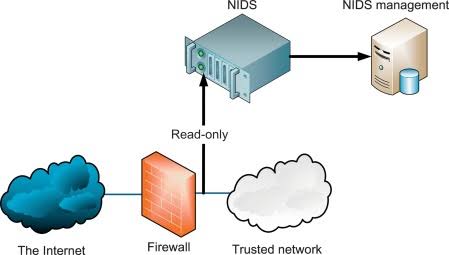
1. NIDS (Network Intrusion Detection System):
Network intrusion detection systems (NIDS) are installed at a predetermined point in the network to analyse traffic from all connected devices.”It keeps track of every subnet traffic and compares it to a database of known risks,” says the company.
The alarm can be issued to the administrator whenever an assault has been detected or strange behaviour has been discovered. Installing an NIDS on the subnet where firewalls are placed to determine if someone is attempting to penetrate the firewall is an example of an NIDS.
2. HIDS (Host Intrusion Detection System):
Host intrusion detection systems (HIDS) are network intrusion detection systems that run on separate hosts or devices. A HIDS only monitors the device’s incoming and outgoing packets, alerting the administrator if suspicious or malicious activity is discovered. It compares the current snapshot to the previous snapshot of existing system files. An alert is given to the administrator if the analytical system files have been modified or removed. The use of HIDS on mission-critical equipment, which are not expected to modify their layout, is an example.
3. PIDS (Protocol-based Intrusion Detection System):
A protocol-based intrusion detection system (PIDS) is a system or agent that is always present at the server’s front end, regulating and interpreting the protocol between the user/device and the server. It is attempting to secure the web server by checking the HTTPS protocol stream on a regular basis and accepting the associated HTTP protocol. Because HTTPS is not encrypted until it reaches the web presentation layer, this system would have to stay in this interface in order to use HTTPS.
4. Application Protocol-based Intrusion Detection System(APIDS)
A system or agent that lives within a collection of servers is known as an Application Protocol-based Intrusion Detection System (APIDS). It detects intrusions by monitoring and analysing application-specific protocol traffic. This would, for example, track the SQL protocol as the middleware interacts with the database on the web server.
5. Intrusion Detection System (Hybrid):
A hybrid intrusion detection system is created by combining two or more intrusion detection technologies. The host agent or system data is merged with network information to create a complete view of the network system in the hybrid intrusion detection system. In compared to conventional intrusion detection systems, the hybrid intrusion detection system is more effective. Hybrid IDS is exemplified by Prelude.
IDS Detection Method:
- Method based on signatures
Signature-based IDS identifies attacks based on specific patterns in network traffic, such as the amount of bytes or the number of 1s or 0s. It also detects malware based on the virus’s previously known dangerous instruction sequence. Signatures are the patterns that the IDS detects.
Signature-based IDS can readily detect attacks whose pattern (signature) is already present in the system, but new malware attacks are difficult to detect since their pattern (signature) is unknown.
- Anomaly-based Approach:
As new malware is generated at a rapid rate, anomaly-based IDS was designed to identify unknown malware threats. Machine learning is used in anomaly-based IDS to construct a trustworthy activity model, and anything that comes in is compared to that model, and it is considered suspicious if it is not found in the model. In comparison to signature-based IDS, machine learning-based IDS has a superior generic property because these models may be trained according to the applications and hardware setups.
Firewalls vs. Intrusion Detection Systems (IDS):
IDS and firewalls are both concerned with network security, however an IDS varies from a firewall in that a firewall searches for intrusions from the outside in order to prevent them from occurring. “Firewalls prevent infiltration by restricting network access; nonetheless, an attack from within the network is undetected.”
An intrusion detection system (IDS) characterises a suspected intrusion after it has occurred and then raises an alarm.
A firewall is more like an Intrusion Prevention System (IPS) than an Intrusion Detection System (IDS) because it is an active protection mechanism. An IPS is similar to an IDS, but instead of simply generating an alarm, it actively inhibits recognised threats.
Many next-generation firewalls (NGFWs) feature integrated IDS/IPS technology, which complements the functionality of a firewall. This allows them to impose specified filtering rules (firewalls) while also detecting and responding to increasingly complex cyber threats (IDS/IPS).
Intruder detection systems (IDS) vs. intrusion prevention systems (IPS)
An intrusion prevention system is similar to an intrusion detection system, except it can be programmed to stop possible threats. IPSes, like intrusion detection systems, can monitor, log, and report on actions, but they can also be set to block threats without the need for a system administrator’s intervention. An IDS merely alerts you to the presence of suspicious activity; it does not prevent it.
An intrusion prevention system (IPS) is often placed between a company’s firewall and the rest of its network, and it can prevent any suspicious traffic from reaching the remainder of the network. Intrusion prevention systems respond to active attacks in real time, catching attackers that firewalls and antivirus software would miss.
IPSes, on the other hand, should be used with caution because they are prone to false positives. Because the IPS blocks legal traffic from passing through, but the IDS just identifies it as possibly malicious, an IPS false positive is likely to be more serious than an IDS false positive.
Most enterprises now require either an IDS or an IPS as part of their security information and event management (SIEM) system, and in many cases both.
Several companies offer unified threat management (UTM), which combines an IDS and an IPS into a single package, allowing enterprises to deploy both simultaneously alongside firewalls and other security systems.
Use of IDS in Networks
An IDS, when installed at a strategic point or points inside a network to monitor traffic to and from all devices on the network, will analyse passing traffic and match traffic on subnets to a library of known threats. The alert can be issued to the administrator once an attack has been detected or anomalous behaviour has been detected.
Techniques of Evasion
Knowing the methods used by cyber thieves attempting to enter a secure network can help IT organisations understand how IDS systems might be used to overlook actionable threats:
- Fragmentation: Sending fragmented packets allows the attacker to remain undetected by the detection system, allowing the attacker to remain undetected.
- Avoiding defaults: A protocol’s port does not always provide information about the protocol being transported. The IDS may not be able to identify the presence of a trojan if it has been modified to utilise a different port by an attacker.
- Low-bandwidth coordinated attacks: coordinating a scan among multiple attackers, or even assigning different ports or hosts to different attackers. This makes it difficult for the IDS to correlate the collected packets and determine whether or not a network scan is taking place.
- Address spoofing/proxying: attackers can obfuscate the source of an attack by bouncing an assault around inadequately secured or mistakenly configured proxy servers. It’s quite tough to determine if the source is faked and bounced by a server.
- Pattern change evasion: In order to detect assaults, IDS rely on pattern matching. “By making simple adjustments to the assault architecture, detection can be avoided.”
Choosing an IDS System
An intrusion detection system (IDS) is an important part of any cybersecurity strategy. Although a simple firewall is the foundation for network security, many advanced attacks can get around it. An IDS adds another layer of defence, making it more difficult for an attacker to obtain unnoticed access to a company’s network.
It’s critical to think about the deployment scenario while choosing an IDS system. In some circumstances, an IDS may be the best option for the job, while in others, an IPS’s integrated protection may be a better alternative. An integrated solution is provided by using an NGFW with built-in IDS/IPS capabilities, which simplifies threat detection and security administration.
Why Do Intrusion Detection Systems Matter?
“Modern networked business environments demand a high level of security to enable secure and accurate information flow across varied businesses.”After traditional security technologies fail, an intrusion detection system works as an adaptable safeguard device for system security. “As cyber-attacks get more sophisticated, it’s important that defensive technology keeps up.”
Intrusion detection systems have a number of advantages.
Intrusion detection systems provide a number of advantages to businesses, starting with the capacity to detect security incidents. An IDS can assist in determining the number and types of assaults. This information can be used to improve security systems or build more effective controls. Companies can also use an intrusion detection system to find vulnerabilities or issues with their network device setups. After then, these measurements can be utilised to assess future threats.
Intrusion detection systems can also assist businesses in meeting regulatory requirements. Companies can gain more visibility throughout their networks using an IDS, making it easier to comply with security standards. Businesses can also include their IDS logs in their documentation to demonstrate that they are satisfying certain compliance criteria.
Security responses can also benefit from intrusion detection systems. Because IDS sensors can detect network hosts and devices, they can also scan data within network packets and identify the operating systems of services being used. Manual censuses of connected systems are inefficient. “Collecting this data with an IDS can be significantly more efficient.”
Conclusion
Because the ultimate purpose of an IDS is to protect the information assets that are at risk and are most valuable to a business, determining the cost-effectiveness of intrusion detection is critical. We looked at cost elements related to intrusion detection in this paper, such as development cost, operational cost, damage cost, and reaction cost. To measure these cost aspects, we’ve proven that an attack taxonomy, as well as organization-specific security policies and priorities, is required. We investigated the trade-offs between these variables and defined consequential cost as the expense associated with an IDS’s predictions. The sum of an IDS’s operating and consequence costs is the overall projected cost.
The ability of an IDS to minimise this total estimated cost demonstrates its cost-benefit. A multiple model machine learning strategy for lowering operational costs and a post-detection decision module for lowering consequential costs were proposed. Our approaches are effective, according to empirical testing utilising the DARPA Intrusion Evaluation dataset.