What Is a SOCKS Proxy ?
Proxy server for each application layer protocol, such as HTTP, HTTPS(controversial), FTP, and many others. For example, for HTTP, you’d use squid, and for HTTPS, you’d use Browsermob proxy, and so on. A SOCKS 5 proxy now provides a universal framework for various protocols to transit data in a transparent and safe manner.
SOCKS, or Socket Secure, is a network protocol that allows clients to communicate with servers through a firewall by routing network traffic to the appropriate server. SOCKS is a network protocol that can handle any form of traffic generated by any protocol or programme.
On behalf of the client, a SOCKS proxy server establishes a Transmission Control Protocol (TCP) connection to another server behind the firewall, then exchanges network packets with the actual server. Because clients are often behind a firewall and are not permitted to make TCP connections to outside servers unless they do so through the SOCKS proxy server, the SOCKS proxy server does not interpret network traffic between client and server in any way. As a result, a SOCKS proxy routes a user’s TCP and User Datagram Protocol (UDP) traffic across the firewall.
SOCKS is a layer 5 protocol that doesn’t care about anything below it in the Open Systems Interconnection (OSI) paradigm, hence it can’t be used to tunnel protocols below layer 5. This contains stuff like ping and ARP (Address Resolution Protocol). Because it works at layer 5, it won’t allow an attacker to scan using tools like Nmap if they’re scanning based on half-open connections from a security standpoint.
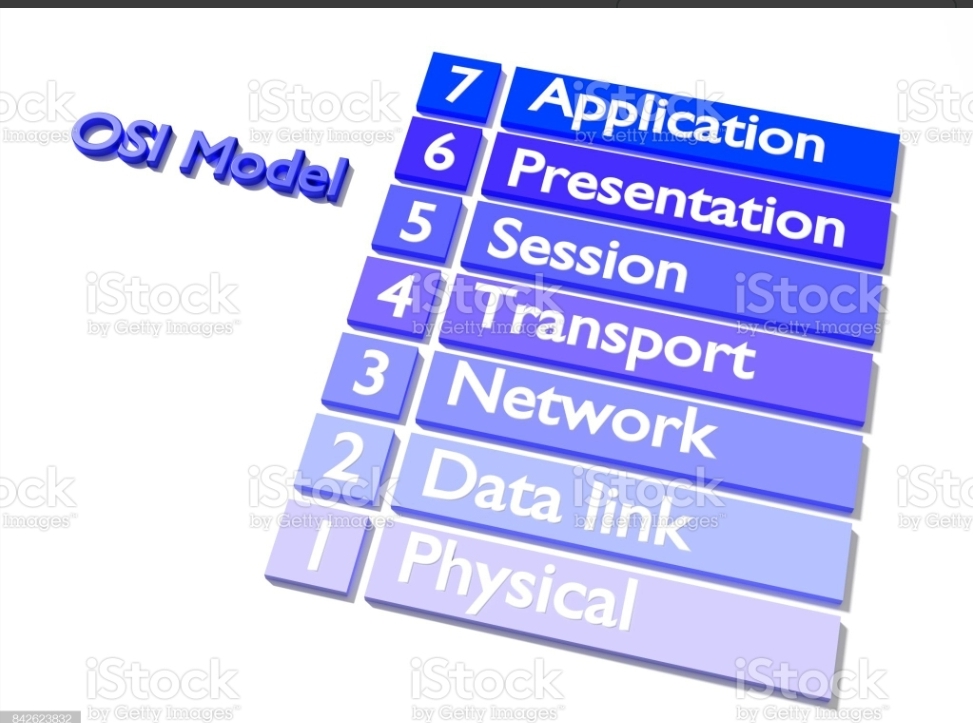
SOCKS can handle a variety of request types, including HTTP, HTTPS, POP3, SMTP, and FTP, because it resides between SSL (layer 7) and TCP/UDP (layer 4). As a result, SOCKS can be used for a variety of purposes, including email, online surfing, peer-to-peer file sharing, and file transfers.
Application proxies are proxies that are developed for specific protocols at layer 7, such as an HTTP proxy that interprets and forwards HTTP or HTTPS traffic between client and server.
SOCKS4 and SOCKS5 are the only two versions available.
The following are the primary changes between SOCKs5 and SOCKS4:
- SOCKS4 does not support authentication, whereas SOCKS5 does; and SOCKS5 offers a wide range of authentication techniques.
2. UDP proxies are not supported by SOCKS4, although they are supported by SOCKS5.
Because it establishes a full TCP connection with authentication and employs the Secure Shell (SSH) encrypted tunnelling mechanism to relay traffic, a SOCKs5 proxy is more secure.
Why Should You Use SOCKs5?
There are four major advantages to employing a SOCKs5 proxy with SSH tunnelling, as listed below.
1. Use a Firewall to Access Back-End Services
To minimise potential security concerns, a cluster is usually hosted in the cloud and protected by a firewall. There are two ways to access any backend services running within a cluster, each with its own set of restrictions:
- Open up backend services to the public (and accept the security risk that comes with it); or
- Allow traffic to backend services by whitelisting the client or user’s IP (this is not the best solution for when a user’s IP changes, though).
An alternative to the two unattractive solutions above is a SOCKs5 proxy with dynamic port forwarding through SSH. Without exposing the backend service ports or whitelisting certain IPs, an administrator or developer could access any backend services inside a cluster hosted in the cloud behind a firewall for debugging, monitoring, and administrating from a public network.
Let’s have a look at an example. When a Hadoop cluster is hosted on the cloud, the administration or monitoring application APIs or web user interface (UI) ports for monitoring it are closed by default for security reasons. You can utilise SSH dynamic port forwarding to master or edge a node cluster to access these APIs or web UIs, because the master node will have a public IP and execute SSH services by default, which is accessible so the user can connect from the outside.
Let’s pretend you’re dealing with a virtual private cloud (VPC). By restricting remote instances’ access to the outside world, you can use a bastion host to securely access them within a VPC. The bastion host is accessible from the outside world, but only port 22 (SSH) is exposed. You can connect to distant instances operating in the VPC using SSH dynamic port forwarding (SOCKs5 proxy).
2. There is no need for any special setup.
SOCKS5 doesn’t require any additional configuration as long as you have SSH access to the cluster’s Edge node or Gateway. As a result, users such as administrators and developers can use an SSH tunnel to access back-end resources beyond the firewall without the need for a virtual private network (VPN).
3. No Public or Free Proxy Server from a Third-Party in Your Deployments
No layer 7 application-related special proxies are required for each service to route application requests because a SOCKs5 proxy directs all types of TCP and UDP traffic to their corresponding service via SSH tunnelling.
4. Better Performance with Fewer Errors
SOCKs5 does not rewrite data packets like other application proxies. It simply transports data between devices. As a result, it is less prone to errors, and performance naturally improves.
In Practice, How Does SOCKs5 Work?
Any CISO would leap at the chance to take advantage of the advantages outlined above. But, in the context of a corporate security strategy, what does a SOCKs5 proxy look like? When it comes to adopting SOCKs5 in their environment, where do security leaders start? Here are some helpful hints to get you started.
SOCKS5 has improved security and now includes three modes of authentication:
- Authentication with no password – To connect to a proxy, no authentication is necessary;
- Authentication through username and password –To connect to a proxy, you must first enter login information.
- Authentication with the GSS-API – To authenticate your identity, both you and the server use operating system-level authentication techniques.
Configuring a SOCKs5 Proxy Connection
The client application must be capable of supporting the SOCKs5 protocol in order to SOCKSify an IT environment. The following syntax is based on the SSH client for Linux; it demonstrates how to set up a SOCKs5 proxy server on your local computer and then authenticate to a cluster’s Edge node or a cloud-hosted gateway that delivers traffic to the cluster’s servers:
- $ ssh -D 30001 root@EdgeNodeSSHserverIP -C -f -N (password: xyz; or $ ssh -D 30001 root@EdgeNodeSSHserverIP -C -f -N (password: xyz; or $ ssh –
- ssh -i /path/to/private key -D 30001 root@EdgeNodeSSHserverIP -C -f -N $ ssh -i /path/to/private key -D 30001 root@EdgeNodeSSHserverIP -C -f -N
The programme above starts the SOCKs5 server and binds to port 30001, then connects to an Edge Node, Master Node, or Gateway Node through a cloud-hosted SSH tunnel.
The above command’s options accomplish the following:
- On the client machine, D 30001 instructs SSH to build a SOCKs5 server on port 30001.
- Before transferring data, C compresses it.
- “Do not execute a remote command,” says N.
- This is useful for forwarding ports simply (protocol version 2 only).
- F instructs SSH to exit the foreground right before the command is executed.
- Using the SOCKs5 Protocol to Connect to Endpoints
Configure your clients to access the cluster’s internal services once a SOCKs5 proxy has been setup. We utilise a command line URL (cURL) that supports the SOCKs5 protocol to make things simple. Other techniques, such as using a web browser, necessitate a little more setup and preparation.
The following cURL command explains how to use the SOCKs5 proxy over the SSH tunnel setup above to access one of the HTTPS application endpoints listening on port 8000 behind a firewall:
- curl -x socks5h://localhost:30001 -v -k -X GET https://EdgeNodeSSHserverIP:8000
On localhost, the cURL tool above connects to port 30001. The SSH client sends the identical request to the SSH server through SSH tunnel after receiving an HTTP GET request on port 30001 from the cURL.
The request is handled by the remote SSH server, which then sends it to a back-end service waiting on port 8000. The client receives the response via the same SSH tunnel to the client’s SOCKs5 proxy. The response is relayed by the proxy to the cURL, which displays it.
You may also use the netcat software to test the TCP connection after you’ve constructed a SOCKs5 proxy using the SSH dynamic port forwarding approach. A TCP connection test is performed with the SOCKs5 proxy for back-end services listening at port 8443, as seen below:
- ncat –proxy 127.0.0.1:30001 –proxy-type socks5 EdgeNodeSSHserverIP 8443 -nv
Is a VPN better than a SOCKS5 proxy?
A VPN is more secure and faster than SOCKS5. It’s easy to mix up a SOCKS5 proxy and a VPN, but there are important distinctions to be made. SOCKS5, like most proxies, will not encrypt your data and will slow down your internet connection.

Furthermore, SOCKS is easily detected, therefore it is unlikely to get you past national firewalls. As a result, you should use a VPN to improve its security.
A decent VPN, on the other hand, encrypts your data as it travels from your device to the VPN server, guaranteeing that no one can see it along the way. You can still get around internet limitations and safeguard your IP address with a service like NordVPN, but you’ll receive true anonymity and lightning-fast internet speeds.
SOCKS5 proxy servers have a number of advantages.
Here are four compelling reasons to employ SOCKS proxies:
1. Allows you to bypass internet blocks
Proxy servers can easily assist you overcome internet blocks since they operate as relays between your device and the internet. If your IP address is blacklisted by a website (or if you use a VPN and its servers’ IP addresses are blacklisted), you can use a SOCKS5 proxy to route your traffic around the block. It will not, however, help you bypass national firewalls in the same way that a VPN will, because most of them employ thorough packet inspection (DPI). This indicates that your ISP has banned your traffic before it reaches the website.
2. Connection that is both faster and more dependable
Unlike its predecessors, which could only utilise the TCP protocol, SOCKS5 proxy servers may also use the UDP protocol, resulting in a more stable connection and better performance.
The TCP internet protocol establishes a connection between a client and a server, ensuring that all packets reach their destination. It necessitates putting the content into a predetermined format so that it may be easily shared. UDP, on the other hand, is not concerned with whether all packets from the client or server arrive at the destination in the same order. The time spent transforming data packets into a stream of fixed packets is not wasted by UDP. As a result, SOCKS5 can provide quicker speeds and a more stable connection with these UDP.
3. Improved overall performance and fewer errors
The headers of data packets are rewritten by several other proxies. As a result, there’s a good probability that data will be misrouted or mislabeled. Because SOCKS5 proxy servers do not alter data packet headers, the risk of mistakes is reduced. The performance naturally improves because there are considerably fewer mistakes. However, because packet headers contain your personal information and may be easily identified, this comes at a cost to your privacy and security.
4. Improved performance on peer-to-peer platforms
Because it transfers smaller data packets, SOCKS5 is faster than other proxies. As a result, it provides higher download rates, which is why so many people utilise it to access P2P sharing websites and platforms.
HTTP proxy vs. SOCKS5 proxy
SOCKS5 proxies can function with any traffic, unlike HTTP proxies, which can only interpret and work with HTTP and HTTPS URLs.
HTTP proxies are high-level proxies that are often tailored to a single protocol. While this improves connection speeds, they lack the flexibility and security of SOCKS proxies. SOCKS proxies are low-level proxies that can handle any software or protocol, as well as any type of communication.
Should you use SOCKS5 with a VPN?
Proxies and VPNs vary primarily in that VPNs encrypt your traffic whereas proxies do not. VPN connections are more reliable than proxy connections, which tend to drop more frequently.
There are few reasons to utilise both at the same time, so pick the best tool for the job. NordVPN servers, fortunately, also allow SOCKS5 connections. For complete instructions on how to use SOCKS5 proxy on various platforms, .
Conclusion
A SOCKs5 proxy is a lightweight, general-purpose proxy that uses a tunnelling mechanism and sits at layer 5 of the OSI model. It can handle a variety of protocols’ traffic, including HTTP, SMTP, and FTP. SOCKS5 is both faster and easier to use than a VPN. Because the proxy uses a tunnelling approach, public cloud users can use SOCKs5 through a secure tunnel like SSH to access resources behind the firewall.



