Blockchain is a system of recording information in a way that makes it difficult or impossible to change, hack, or cheat the system.
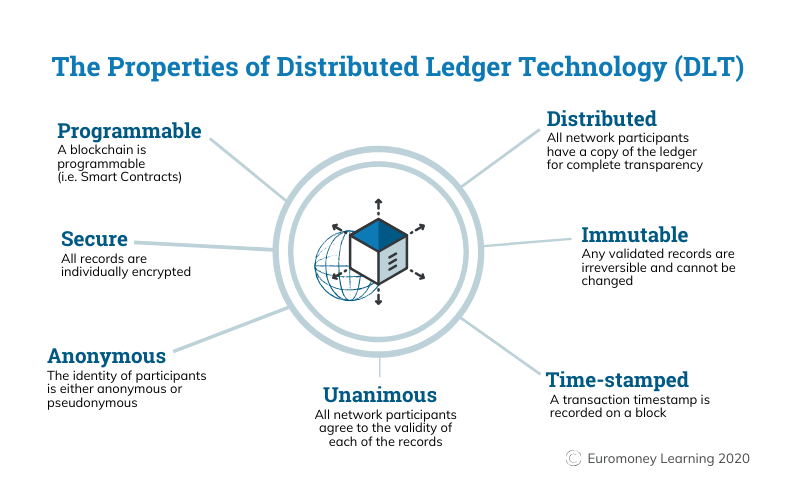
A blockchain is essentially a digital ledger of transactions that is duplicated and distributed across the entire network of computer systems on the blockchain. Each block in the chain contains a number of transactions, and every time a new transaction occurs on the blockchain, a record of that transaction is added to every participant’s ledger.
The decentralised database managed by multiple participants is known as Distributed Ledger Technology (DLT). Blockchain is a type of DLT in which transactions are recorded with an immutable cryptographic signature called a hash.
Blockchain Use Cases for Cybersecurity
Although not unbreakable, blockchain has evolved to become one of the most foolproof forms of transacting in the digital network realm.One of the best uses would be utilising its integrity assurance for building cybersecurity solutions for many other technologies.

1. Securing Private Messaging
With the internet shrinking the world into a global village, more and more people are joining social media.Huge amounts of metadata are collected during these interactions. Most social media platform users protect the services and their data with weak, unreliable passwords.
Most messaging companies are warming up to blockchain for securing user data as a superior option to the end-to-end encryption which they currently use. Blockchain can be used to create a standard security protocol. For enabling cross-messenger communication capabilities, blockchain can be used to form a unified API framework.
2. IoT Security
With the current obsession for Artificial Intelligence (AI), it has become easier for hackers to access overall systems like home automation through edge devices like ‘smart’ switches. In most cases, a large number of these IoT devices have sketchy security features.
In this case, blockchain can be used to secure such overall systems or devices by decentralising their administration. The approach will give the capabilities of the device to make security decisions on their own. Not depending on the central admin or authority makes the edge devices more secure by detecting and acting on suspicious commands from unknown networks.
3. Verification of Cyber-Physical Infrastructures
Data tampering, systems misconfiguration together with component failure have spoiled the integrity of information generated from cyber-physical systems. However, the capabilities of blockchain technology in information integrity and verification may be utilised to authenticate the status of any cyber-physical infrastructures. Information generated on the infrastructure’s components through blockchain can be more assuring to the complete chain of custody.
4. Protecting Data Transmission
Blockchain can be used in the future to prevent unauthorized access to data while in transit. By utilising the complete encryption feature of the technology, data transmission can be secured to prevent malicious actors from accessing it, be it an individual or an organisation. This approach would lead to a general increase in the confidence and integrity of data transmitted through blockchain.
5. Decentralising Medium Storage
Most companies still use the centralised form of the storage medium. To access the entire data stored in these systems, a hacker simply exploits but a single vulnerable point. Such an attack leaves sensitive and confidential data, such as business financial records, in the possession of a criminal.
By using blockchain, sensitive data may be protected by ensuring a decentralised form of data storage. This mitigation method would make it harder and even impossible for hackers to penetrate data storage systems. Many storage service companies are assessing ways blockchain can protect data from hackers. Apollo Currency Team is a good example of an organisation that has already embraced the blockchain technology in their systems (The Apollo Data Cloud).
Conclusion
No matter how it is utilised, the key component of blockchain technology is its ability to decentralise. This feature removes the single target point that can be compromised. As a result, it becomes nearly impossible to infiltrate systems or sites whose access control, data storage, and network traffic are no longer in a single location. Therefore, blockchain may be one of the most efficient mitigation strategies for cyber threats in the coming days.











