The world is moving towards the quantum revolution. Quantum computers give access to unparalleled processing power. However, with all the advantages, we are also faced with unprecedented challenges which the conventional cybersecurity tools cannot help mitigate. However, in this context, the quantum cryptography techniques, or more accurately, the quantum key distribution methods can prove to be beneficial.
What is Quantum Cryptography?
Cryptography is the process of encrypting data, or converting plain text into scrambled text so that only someone who has the right “key” can read it. Quantum cryptography, by extension, simply uses the principles of quantum mechanics to encrypt data and transmit it in a way that cannot be hacked.
.
While the definition sounds simple, the complexity lies in the principles of quantum mechanics behind quantum cryptography, such as:
- The particles that make up the universe are inherently uncertain and can simultaneously exist in more than one place or more than one state of being.
- Photons are generated randomly in one of two quantum states.
- You can’t measure a quantum property without changing or disturbing it.
- You can clone some quantum properties of a particle, but not the whole particle.
All these principles play a role in how quantum cryptography works.
How Does It Work?
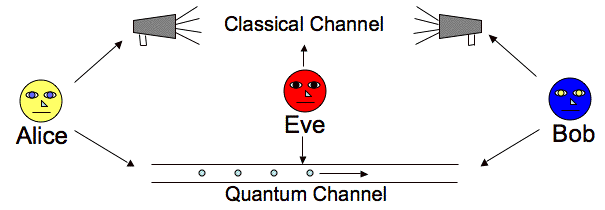
Quantum cryptography, or quantum key distribution (QKD), uses a series of photons (light particles) to transmit data from one location to another over a fiber optic cable. The photons travel to a receiver, which uses two beam splitters (horizontal/vertical and diagonal) to “read” the polarization of each photon.
Advantages
- It revolutionizes secure communication by providing security based on fundamental laws of physics instead of mathematical algorithms or computing technologies used today.
- It is virtually unhackable
- It is simple to use
- Less resources are needed in order to maintain it
Disadvantages
- The world wide implementation of this can take up lots of jobs and hence unemployment will increase.
- It lacks many vital features such as digital signature, certified mail etc.
- While traveling through the channel (i.e. optical fiber or air), there is possibility of change in polarization of photon due to various causes.
- The largest distance supported by QKD is about 250 KM at a speed of 16 bps through guided medium.
Applications of Quantum Cryptography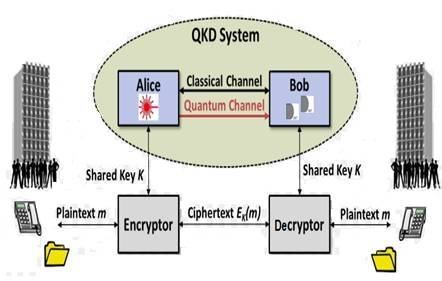
- Early this year, Chinese and Austrian researchers streamed the first quantum-encrypted video call.
- In 2017, Oxford University researchers, collaborating with Nokia and Bay Photonics, created a system for transmitting quantum keys that could be used in PoS systems.
- It is used to protect the networks .
CONCLUSION
Current cybersecurity best practices call for multiple security layers.I expect that will remain true even as we perfect quantum technology. While the capabilities that quantum cryptography offer are powerful, a hybrid solution will likely be the best approach. In the short term, post-quantum cryptography looks more promising as a widely deployed solution.