Fileless malware is a type of malicious activity that uses native, legitimate tools built into a system to execute a cyber attack. Unlike traditional malware, fileless malware does not require an attacker to install any code on a target’s system, making it hard to detect.
Characteristics of Fileless Malware
- Leverages approved applications that are already on the targeted system
- No identifiable code or signature that could be detected by traditional AV solutions
- May remain in environment despite white listing and sandboxing measures
- No particular behavior that could be detected by heuristics scanners
- Memory-based: lives in system memory
- Uses processes that are built into the operating system
- Can be paired with other types of malware
How does it works?
Fileless malware can use your system’s software, applications and protocols to install and execute malicious activities.
- Phishing emails, malicious downloads, and links that look legitimate as points of entry.
- Legitimate-looking websites that actually are malicious.
- Applications you’ve already installed, like Microsoft Word or JavaScript.
- Native and highly trusted applications like Windows Management Instrumentation (WMI) and Microsoft PowerShell.
- Lateral infiltration.
Common Techniques
- Exploit kits
- Registry resident malware
- Stolen credentials
- Memory-only malware
- Hijacked native tools
- Fileless ransomware
Stages of Fileless Attack
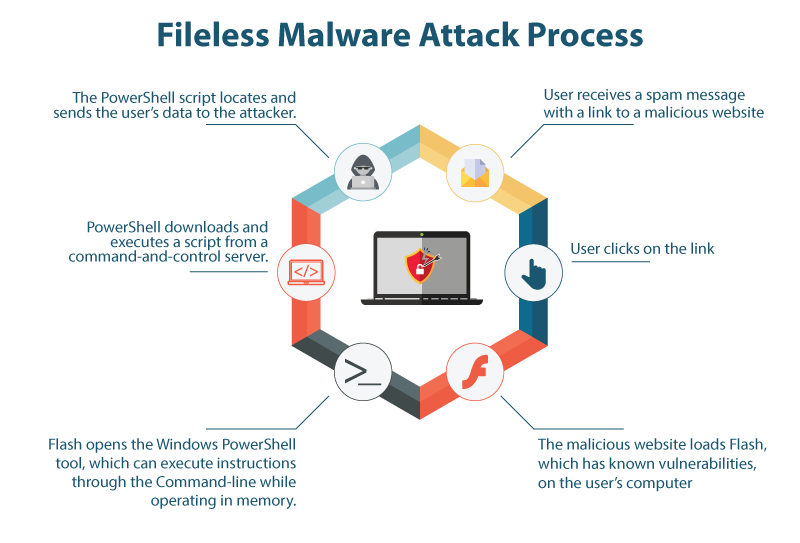
- Gain Access
- Steal Credentials of user
- Maintain Persistence i.e., Now, the attacker set up a backdoor that will allow him to enter in your environment, without repeating initial steps of attack.
- Exfiltrate Data : Attacker gather the data from your location and replicates it to his own location for access.
Protection against Fileless Malware
- Being careful when downloading and installing applications.
- Keeping up-to-date with security patches and software applications.
- Updating browsers.
- Watching out for phishing emails.
Summary
The threats of fileless malware is real. But, the awareness and conscientiousness prevent us from these kind of attacks. Security team need to think beyond intruders to prot













[…] is a form of malware that encrypts a victim’s files. The attacker then demands a ransom from the victim to […]