Suddenly thinking we can’t decide what it is, but the person who is well worse in these topic can decide whether to call it parasitic computing or hacking.
These both are the two sides of the same form.one is formal and other is informal. and making usage of these two forms is still on the people and how do they use for their personal works.
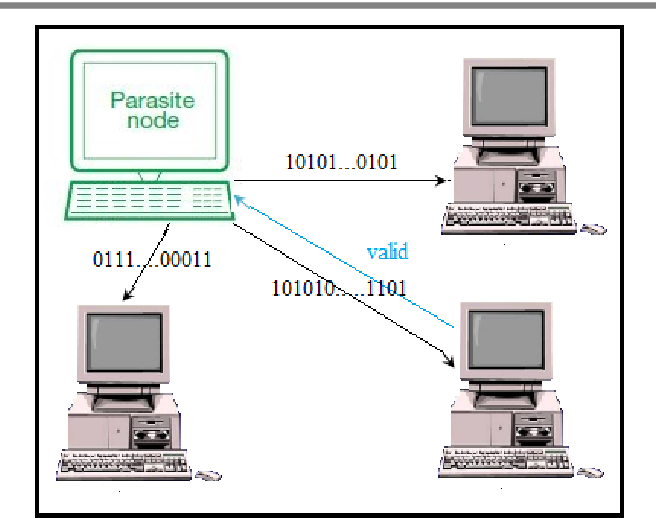
Parasitic computing is a technique in which one computer or server links to other servers and uses that equipment to provide computation capacity.
It is normally not considered hacking, or theft of computer services, because the program does not defeat any locks or safeguards on the other equipment.
Rather, a legitimate message can be delivered to the other computers, and they will provide computing capacity without any breach of security.
OR

FUTURE SCOPE OF PARASITIC COMPUTING:
In parasitic computing, host machine uses CPU and computational resources of other machines connected over the same network.
The underlying purpose is primarily to solve metaheuristic problems, for which there is no defined algorithm to find its solution, but we can assess how good a given candidate solution is.
Thus, in case of metaheuristic problems, there exists large number of candidate solutions each of which requires evaluation. In parasitic computing, we make use of remote computers over.
FEATURES OF PARASITIC COMPUTING:
1.parasitic computing theoretically offers the chance to use the vast computational power of the whole Internet.
2.Several large computational problem can be solved by engaging various web servers physically located in different parts of the world, each of which unknowingly participated in the experiment.
3.ethically challenging alternative for cluster computing, as it uses resources without the consent of the computer’s owner.
4.parasitic computing does not compromise the security of the targeted servers, and accesses only those parts of the servers that have been made explicitly available for Internet communication.
DISADVANTAGES:
Communication to computation ratio: Currently, Internet-wide parasitic problem solving is only a theoretical consideration, because the method employed by Mr Barabási and his colleagues is “computationally inefficient”, as they admit.
They had to invest hundreds of machine cycles to send and receive messages until they finally achieved the solution to their mathematical problem.
To make parasitic computing really useful, the ratio between the invested communication and the resulting computation has to be dramatically improved.
The Notre Dame researchers suggest that exploiting HTTP or encryption/decryption could solve the efficiency problem.
Delayed Services :The legal aspects of parasitic computing are far from clear. The security of the target computer is in no way compromised.
It is just simple communication, using only areas specifically earmarked for public access. But it could slow machines down by engaging them in a computational conversation, which would be similar to the disruption of Internet services by a denial-of-service attack.
And there is only one way to prevent the parasites from sucking computational power out of your computer –disconnecting it.
CONCLUSION:
There is lot much is there to know about the parasitic computing. even I got know while writing the blog itself. and I call it has hacking as it also leads to criminal activities.
Parasitic computing moves computation onto what is logically the communication infrastructure of the Internet, blurring the distinction between computing and communication.












