Biometric authentication is a cybersecurity process that verifies a user’s identity using their unique biological characteristics as their password. By comparing a user’s biometric signature against one submitted and stored in a database, biometric authentication systems are able to determine whether the person is attempting to log in/access data/etc. Is actually who they say they are.
Biometric authentication is a rapidly evolving technology that can – if implemented correctly – help your business ensure that only the right people have access to sensitive information.
How biometric authentication works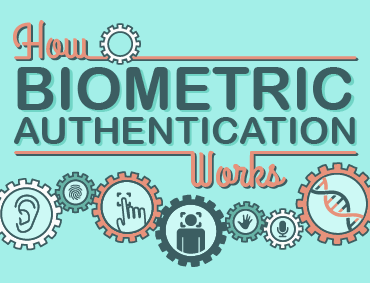
Biometric authentication works by comparing two sets of data: the first one is preset by the owner of the device, while the second one belongs to a device visitor. If the two data are nearly identical, the device knows that “visitor” and “owner” are one and the same, and gives access to the person.
The important thing to note is that the match between the two data sets has to be nearly identical but not exactly identical. This is because it’s close to impossible for 2 biometric data to match 100%. For instance, you might have a slightly sweaty finger or a tiny, tiny scar that changes the print pattern.
Popular biometric authentication methods
- Fingerprint Scanners
- Fingerprint Scanners
- Speaker recognition
- Facial recognition
Cybersecurity and Biometrics
The storage of biometric data is another concerning factor of biometric identification. As information stored increases, security-related incidents come in the picture which consequently leads to compromising data of millions of users every year. Because of attacks on this stored information financial data, personal details and passwords are exposed too. 
Today attempts to bypass data security events look like efforts to bypass the impossible thing. Notwithstanding the concern of data security efforts falling short, they have to be used. Information systems carrying a lot of biometric data of students, employees or citizens are a possible target of cyber-criminals.
Theft of biometric data can be ruinous. Unlike passwords, biometric identifiers of an individual cannot be changed if compromised. If a criminal can create a pattern out of biometric templates, people can lose their biometric identity permanently, and this is a cybersecurity threat.
Biometric identification technology utilised on mobile gadgets gives sub-standard security than dedicated biometric systems. For instance, fingerprint identification on a cellphone utilises a partial fingerprint recognition algorithm.
The sensor itself is so small that it cannot provide the full fingertip. These dangers with biometrics in the mobile phone can be decreased with constant research and development.
Conclusion
Increase of biometrics lock in cell phones has also exhibited a newer form of risks. Assistance providers are slowly integrating biometrics to verify user entree for their services. Several banks and financial institutions throughout the globe have integrated fingerprint or face recognition ability in their mobile banking applications.







[…] Authentication with high precision Fujitsu has confirmed that the system has a false acceptance rate of less than 0.00008 percent and a false rejection rate of 0.01 percent when the hand is held over the device three times during registration, with one retry for comparison during authentication, using data from 140,000 palms from 70,000 people. […]