Security is the significant challenge that we are facing in this digital era. improper device updates, lack of efficient and robust security protocols, user unawareness, and famous active device monitoring are among the challenges that IoT is facing.
IoT Risks
- Risks that are typical in any Internet system
- Risks that are specific to IoT devices
- Safety to ensure no harm is caused by misusing actuators, for instance.
IoT Threats
| Threats | Attack Procedure | Security Requirement | Examples |
| Physical attacks | Tamper with the hardware and other components. | Tamper resistance | Layout reconstruction, micro-probing |
| Environment attacks | The device encryption key can be discovered by the attacker by recovering the encryption information. | Secure encryption scheme | Timing attack, side- channel attack, fault analysis attack |
| Cryptanalysis attacks | Find ciphertext to break the encryption. | Secure encryption scheme | Known-plaintext attack, chosen plaintext attack |
| Software attacks | Exploit vulnerabilities in the system during its own communication interface and inject malicious codes. | Proper antivirus update | Trojan horse, worms, or viruses |
IoT Challenges
- Scalability
- Connectivity
- End-to-End Security
- Authentication and Trust
- Identity Management
- Attack-Resistant Security Solution
Scalability
Managing a large number of IoT nodes requires scalable security solutions. Because we will be running long sessions while using IoT devices which results in low processing power and storage.
Connectivity
In IoT communications, connecting various devices of different capabilities in a secure manner is another challenge. Because we are connecting each smart device of our home to it.
End-to-End Security
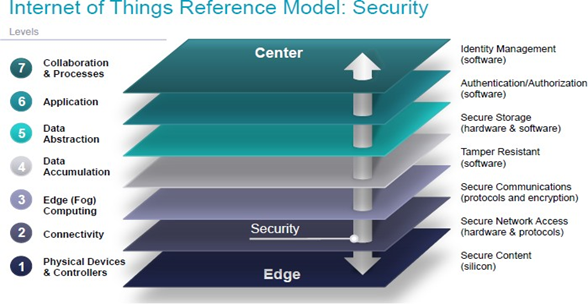
End-to-end security measures between IoT devices and Internet hosts are equally important. It is related to connectivity, when we connect all the devices to main port then our data will be shared to host end, so encryption is really important at their end.
Authentication and Trust
Proper identification and authentication capabilities and their orchestration within a complex IoT environment are not yet mature. This prevents establishment of trust relationships between IoT components, which is a prerequisite for IoT applications requiring ad-hoc connectivity between IoT components, such as Smart City scenarios.
Trust management for IoT is needed to ensure that data analytics engines are fed with valid data. Without authentication it is not possible to ensure that the data flow produced by an entity contains what it is supposed to contain.
Identity Management
Identity management is an issue as poor security practices are often implemented. For example, the use of clear text/Base64 encoded IDs/passwords with devices and machine-to-machine (M2M) is a common mistake. This should be replaced with managed tokens such as JSON Web Tokens (JWT) used by OAuth/OAuth2 authentication and authorization framework (the Open Authorization).
Attack-Resistant Security Solution
Diversity in IoT devices results in a need for attack- resistant and lightweight security solutions. As IoT devices have limited compute resources, they are vulnerable to resource enervation attacks.
Summary
Using IoT devices is not a issues but we have to be aware of its pros and cons and maintain overall security so that no intruder can enter into our proximity.












[…] As the number of connected devices continues to rise, our living and working environments will become filled with smart products – assuming we are willing to accept the security and privacy trade-offs. Regardless of whether you have IoT devices already in use or are considering adopting IoT devices in your organization, make sure you’re prepared to handle the unique security challenges presented by IoT devices. […]