Mobile security or more specifically mobile device security, is the protection of smartphones, tablets, and laptops from threats associated with wireless computing. It has become increasingly important in mobile computing. Of particular concern is the security of personal and business information now stored on smartphones.
Mobile devices are part and parcel of today’s increasingly distributed workforce. Laptops, smartphones, and tablets are provisioned by enterprises to increase employee productivity, while providing flexibility to work remotely.
Attacks based on communication
- Attack based on SMS and MMS
- Attacks based on the GSM networks
- Attacks based on Wi-Fi
- Bluetooth-based attacks
- Attacks based on vulnerabilities in software applications
- Attacks based on hardware vulnerabilities
Mobile Security Threats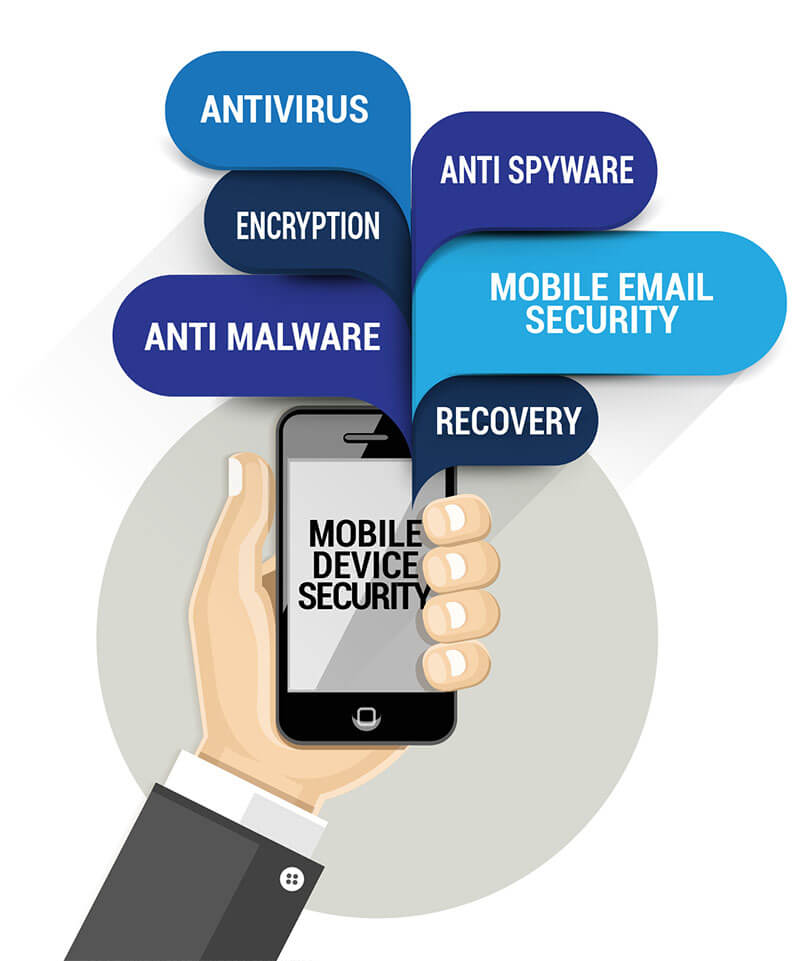
Communicating mobile security threats and best practices has become a central objective due to the ongoing discovery of new vulnerabilities of mobile devices. To cope with this overarching issue, the goal of this paper is to identify and analyze existing threats and best practices in the domain of mobile security.
To this end, the results show high awareness of the threats and their countermeasures in the domain of mobile applications.The study results contribute to the theory on mobile security through the identification and exploration of a variety of issues, regarding both threats and best practices.
How to Secure Your Mobile Device ?
1. USE STRONG PASSWORDS/BIOMETRICS
Strong passwords coupled with biometric features, such as fingerprint authenticators, make unauthorized access nearly impossible. Your passwords should be eight or more characters long and contain alphanumeric characters. Use two-factor authentication.
2. ENSURE PUBLIC OR FREE WI-FI IS PROTECTED
Everybody loves free Wi-Fi, especially when the data plan is inexpensive. But cheap can turn expensive in a very devastating manner. That’s because most of the free Wi-Fi points are not encrypted. These open networks allow malicious people to eavesdrop on the network traffic and easily get your passwords, usernames and other sensitive information.Use WPA for protection against Wi-Fi.
3. UTILIZE VPN
A VPN will enable you to connect to a network securely.It is also useful when accessing sites that are less secure. Non-HTTPS sites are visible to anyone who knows how to use networking and vulnerability tools. These sites are prone to MITM (Man-in-the-middle) attacks, which pave a way to eavesdropping and password sniffing.
4. ENCRYPT YOUR DEVICE
Most mobile devices are bundled with a built-in encryption feature. Encryption is the process of making data unreadable.his is important in case of theft, and it prevents unauthorized access.Most importantly, you need to remember the encryption password because it’s required every time you want to use your mobile device.
5. INSTALL AN ANTIVIRUS APPLICATION
The files you download and the apps you install on your mobile device might be packed with malicious code. Once launched, this code could send your data to hackers.To avoid this, installing a reputable antivirus application will guarantee your security.
Some antivirus applications also offer more functionalities, such as erasing your data if you lose your mobile device, tracking and blocking unknown callers who might be a threat, and telling you which applications are not safe.
6. UPDATE TO THE LATEST SOFTWARE
New loopholes might be exploited leaving your device open to threats, to avoid that, always update your firmware/device. Major mobile device firmware companies, such as Google Android and Apples iOS, roll out new updates from time to time. Most of those updates act as a security patch to known vulnerabilities on your device.
OTHER THINGS TO CONSIDER
- Avoid turning on autofill : ome websites and applications will automatically fill in your username when you visit them. This is due to the autofill feature. Turn it off yo avoid such threats.
- Log out : After using mobile applications, especially those that are linked to one another, such as google applications, ensure that you log off each time you are done using them.
- Use only trusted stores – You should download apps from secure stores. This depends on the platform your mobile device uses.
CONCLUSION
The topic describes the challenges of provisioning and managing security in mobile phone environments and explains how a well-designed deployment system can alleviate these challenges. Making our mobile device secure is not an easy task, but it should be our first priority. As there are new vulnerabilities found every day, it’s important to make sure that we are aware of any suspicious activity that occurs on our device.